The customer chose to protect their confidential information
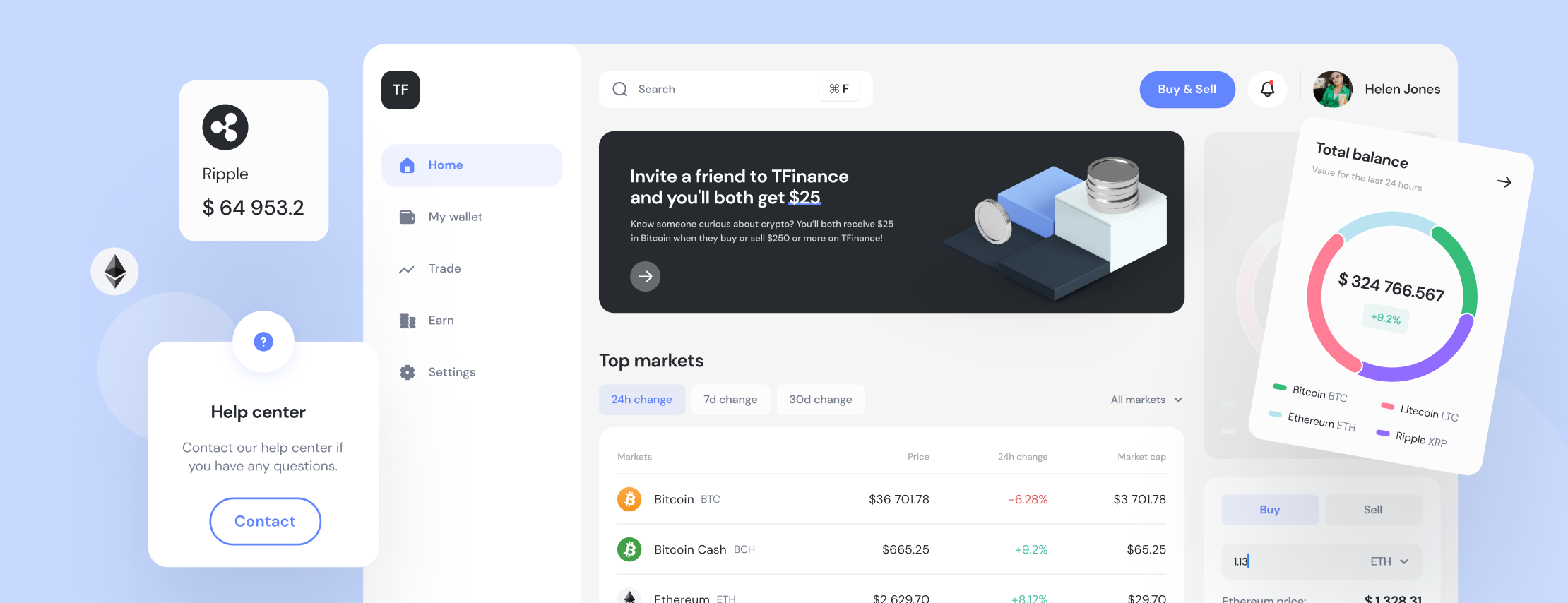
Software for International Trade
About project
Product vision
A set of FinTech tools and software products was engineered to facilitate international commerce and trade. These international trade software solutions enable importers and exporters to transact with each other in a more transparent and efficient fashion. The umbrella term "trade finance” covers the entire range of IT products that banks and companies apply to make such seamless transactions possible.
The core functionalities of the solutuion make it possible to easily include new parties in transactions and mitigate various supply and payment risks. Namely, they enable exporters to obtain receivables or payments in accordance with an agreement, while importers might be granted extended credit to fulfill an order.
The trade finance solution can be used by:
- Banking institutions;
- Insurance companies;
- Importers and exporters;
- Trade finance companies;
- Export service providers and credit agencies.
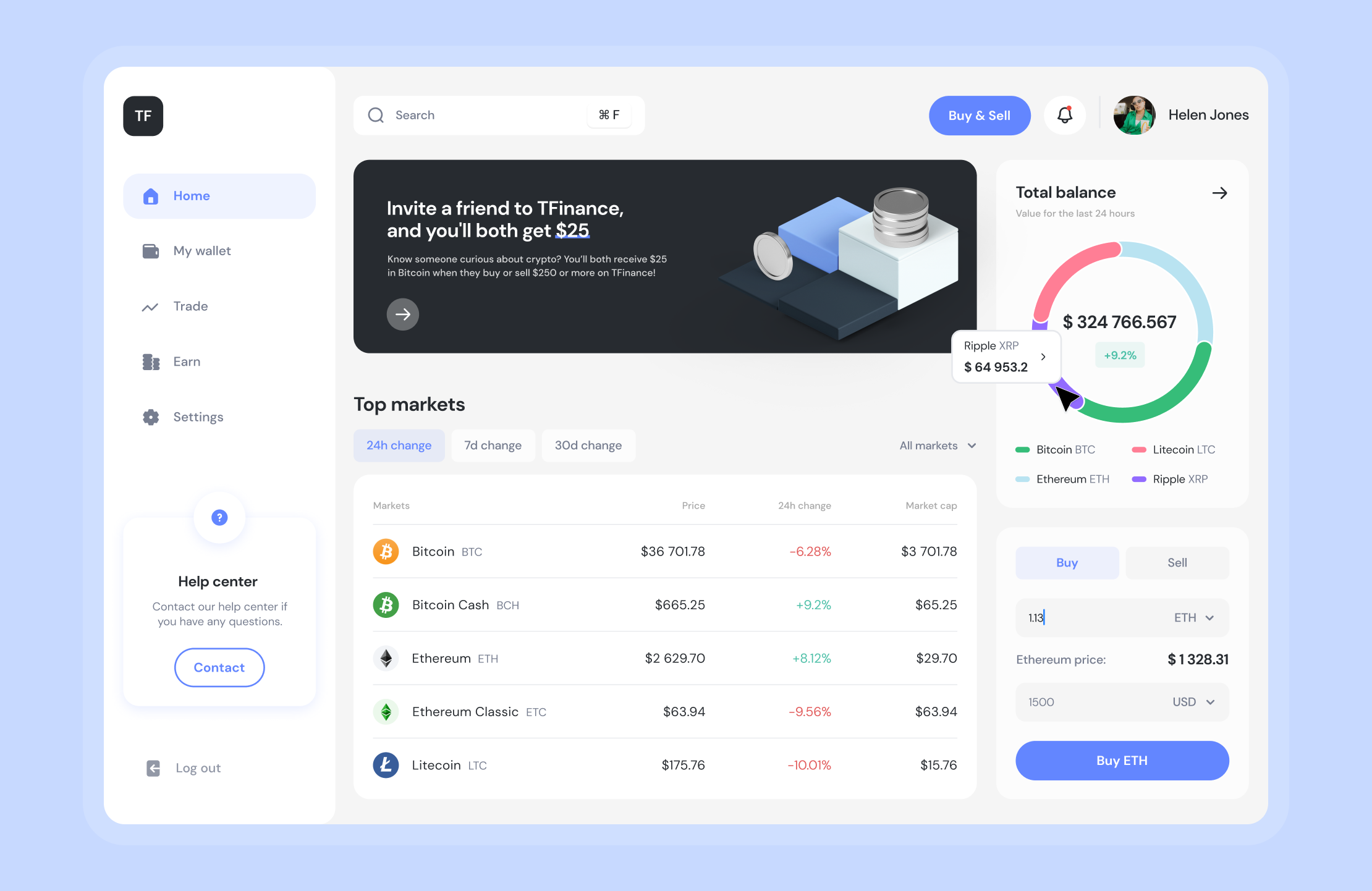
Finance instruments and processes covered:
- Lending lines provided by banking institutions for both exporters and importers;
- Letters of credit issued to mitigate typical risks associated with global trade;
- Processing of agreements abided by all transaction parties;
- Nonpayment risk management by shipping protection and goods delivery insurance.
Andersen's solution delivered:
- AI functionality to make the filtering process more effective;
- Automated screening and OCR of documents to facilitate and speed up compliance checks;
- Integration with a third-party finance software solution to store and share data with trusted partners;
- Automatically built charts to optimize business processes, performance, and flows;
- ML-enabled pipeline chain optimization.
25%
75%
85%
Architecture
Due to ongoing changes in the regime of international sanctions and finance regulations, financial institutions face higher compliance risks and regulatory fines. Under these circumstances, the checking process of non-standard documents poses serious challenges and generates significant compliance risks. On top of that, human errors are also a factor to be reckoned with.
Thus, the solution was expected to be able to run KYC/AML/sanctions checks, scan and process information from all documents via AI, and transfer this data to the target system used by potential end-users for client onboarding, monitoring, and trade validation.
I. Document recognition engine:
- Recognizes characters;
- Identifies document types;
- Scans each field type and value;
- Recognizes buyers, sellers, and their banks.
II. Refinement engine:
- Uses the KYC (Know Your Customer) approach;
- Extracts information about internal and external clients;
- Builds relationship graphs;
- Finds out whether any company in the chain is on sanction, terrorist, or corruption lists.
III. Data Lake engine:
- Uses different sources, both internal and external, for analysis;
- Downloads, filters, generalizes, and sorts out heterogeneous data.
IV. Share engine:
- Ensures that all authorized parties can share documents and sign them.
V. Flexible Machine Learning platform:
- Describes goods and converts codes;
- Builds links between goods, client profiles, and their transactions;
- Recognizes connections between transaction costs and client profiles;
- Prevents insufficient or inaccurate information;
- Scans transactions and payments associated with higher risks of terrorism or corruption;
- Monitors frequently changing addresses and clients from blacklisted and high-risk countries;
- Finds out whether clients participate in high-risk operations;
- Evaluates delivery chains;
- Recognizes smurfing transactions (i.e., those split into several smaller transactions in order to avoid detailed client identification);
- Finds other kinds of alarming information.
VI. KYC/AML risk matrix engine:
- Analyzes and calculates corruption probabilities.
VII. SWIFT process automation:
- Integrates with bank Back-end systems and uses BPM engines to automate SWIFT transactions.
Let's talk about your IT needs
What happens next?
An expert contacts you after having analyzed your requirements;
If needed, we sign an NDA to ensure the highest privacy level;
We submit a comprehensive project proposal with estimates, timelines, CVs, etc.
Customers who trust us


